In my view, it is also superior for an ordinary dwelling person not to employ pirated (hacked) systems, even Regardless of the Virtually zero hazard of falling under the post. All things considered, a hacked technique or software is usually unstable. And what is actually halting pirate hackers from Placing some sort of trojan or adware into your code?
pstree Command in Linux with Examples The pstree command in Linux is a powerful tool that shows jogging processes like a tree framework.
If you are a kind of who use Vim, I love you. You will be happy to know you could password-defend files in Vim utilizing the vim +X filename command, or the :X command specifically in Vim.
And that’s the detail. A lot of people use ls -l to listing the contents with the directory, whereas the exact same can be achieved with the following command:
There are numerous solutions to work with Using the ping command, ping displays tackle as a hostname, so if you need to see them in numbers, make use of the ping -n command; ping -i to specify the interval concerning transmissions, because the default is 1 next.
If you're Unquestionably new to it, Now we have a series of tutorials that will help you get rolling with standard Linux commands.
In situations where you have to evaluate the logs while the applying is functioning, You may use the tail command with -file solution.
As an example, we wish to copy information but don’t know the right commands. That’s why Now we have executed the following command while in the command line:
Latest Linux distributions Use a shell preconfigured for this command. This can save you a couple of keystrokes.
This circumstance is all far too common to Linux users who trust in command-line interfaces for his or her everyday jobs. The excellent news is always that Linux presents robust options to this common Problem, empowering consumers to keep up workflow continuity while not having to overcomplicate duties.
Note: This technique is on no account significantly less safe than fundamental get more info authentication. It may even be safer Should your local method is protected. If you do not compromise the private vital, you won't be capable of log in to SSH.
Assistance from readers such as you retains this weblog working. Acquiring me a cup of coffee is a straightforward and economical way to point out your appreciation and help keep the posts coming!
One of the better Linux command line tricks to get rid of a running command or procedure is to work with Ctrl+C. If you'd like to stop a command operating while in the foreground, You should utilize this keyboard shortcut correctly. It really works in all terminals recognised to me.
Although some consumers appreciate the ability and efficiency of those tools, Other folks call for enhancements in person expertise to make Linux additional interesting to the broader audience.
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
Visit Profile
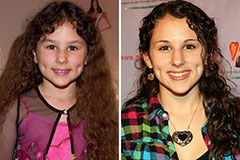 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Tatyana Ali Then & Now!
Tatyana Ali Then & Now!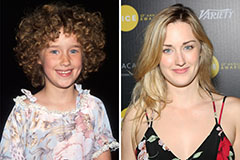 Ashley Johnson Then & Now!
Ashley Johnson Then & Now! Melissa Joan Hart Then & Now!
Melissa Joan Hart Then & Now! Morgan Fairchild Then & Now!
Morgan Fairchild Then & Now!